Cossack Labs’ security engineers analysed several React Native financial applications which have 100+ direct dependencies, including 16 cryptographic ones, to show you the state of the React Native open source.
As we work with security-sensitive applications and React Native is more than popular nowadays, we bravely dived into the research. Here we publish just some figures, but you can read the full article in our engineering blog post too.
Let’s take a look at a simple application that allows users to transfer money from one to another. It has many 3rd party dependencies.
🔎 Dependencies
Believe it or not:
🚩 12.6% of the examined dependencies have known vulnerabilities (maintainers know about the issues, but they are not resolved).
🚩 17.2% look abandoned: they do not have any activities for more than a year.
🚩 2.3% have just a few contributors (in some repositories less than 5 ones).
🚩 2.3% have more than 500 opened issues on GitHub.
🚩 16.1% have more than 100 opened issues.
🔔 So, 12.6% of libraries are already vulnerable, and 37.9% are being so poorly maintained that they are the first candidates to become vulnerable soon.
The green half of the circle, “good dependencies”, looks much better at a glance, but remember it means that only half of all the libraries used in the apps “look okay-ish”.
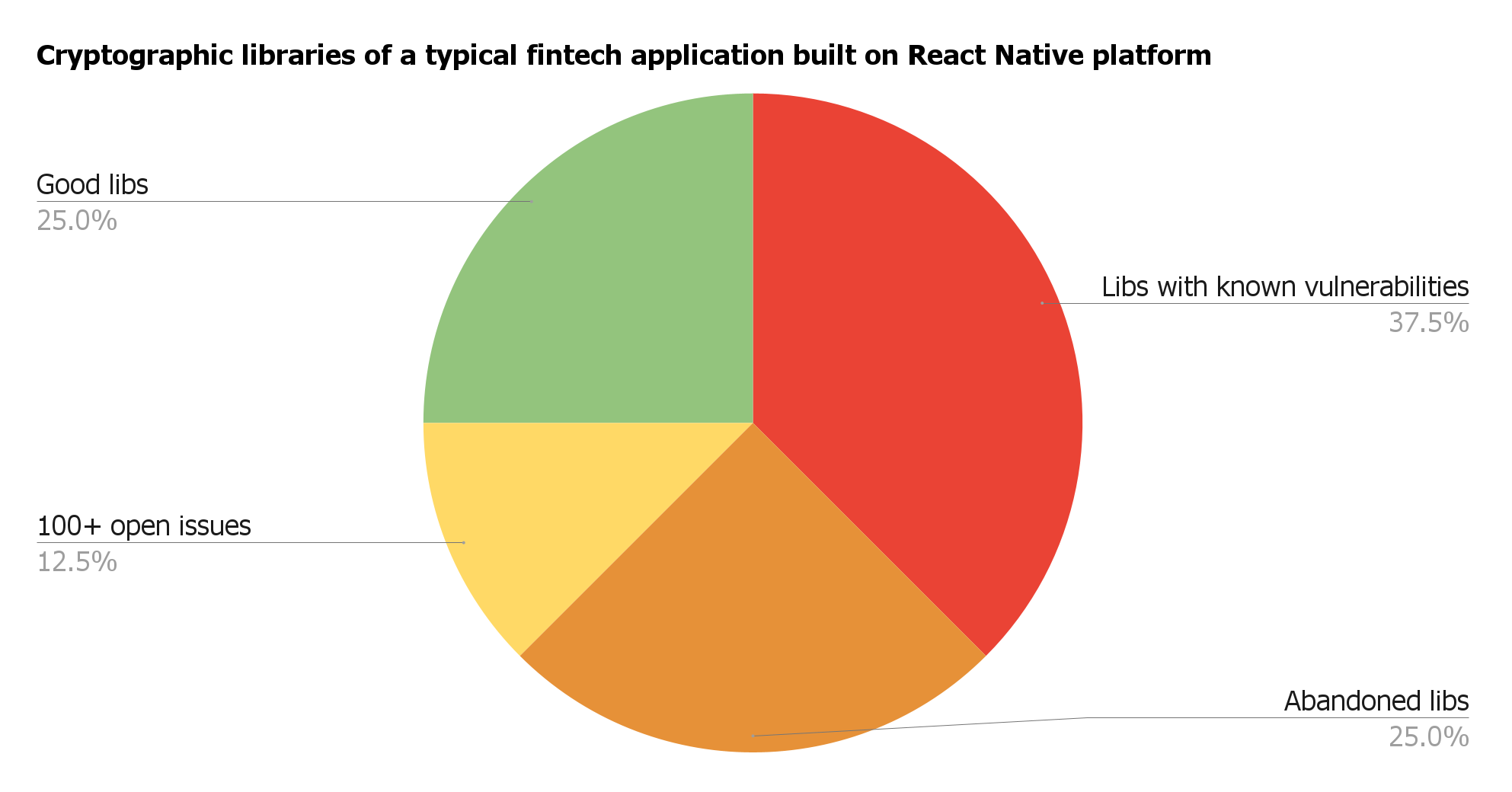
🔎 Cryptographic and security libraries
As we’re data security and cryptography engineers, we came further to examine cryptographic and security libraries. They are especially important as they are used to protect the most valuable assets and simplify developer’s life.
🚩Here’s a picture that we’ve got: with 25% of “good” dependencies, we see 37.5% with already known vulnerabilities, 25% of abandoned projects, and 12.5% one with 100+ opened issues.
🔔 It means that 3/4 libraries used to encrypt data or get access to the Keychain / Keystore, are flawed!
Well, no wonder why finding a good React Native security library is not an easy task...
Read more details about the research and examples of red flags in our long engineering post. Also, we’ve prepared a small guide on How to select a good cryptographic library.
And may the force be with you!


](https://media2.dev.to/dynamic/image/width=800%2Cheight=%2Cfit=scale-down%2Cgravity=auto%2Cformat=auto/https%3A%2F%2Fdev-to-uploads.s3.amazonaws.com%2Fuploads%2Farticles%2F3r8lorfrcbr727ouuk8s.png)






Top comments (0)