What is social engineering?
Social engineering is one of the oldest forms of malicious or unethical hacking. Scammers and con artists have used social engineering long before computers and the internet were ever created. The first social engineering attack comes from the story or legend of the Trojan Horse. According to legend, the Greeks hid inside a wooden horse and tricked the Trojans into letting them into the gated city.
Photo by Tayla Kohler / Unsplash
Another example of social engineering is the well-known Nigerian Prince email scam. You may think that the seemingly obvious scam is a new invention that came about because of low-cost email sending (cast a wide net, eh?), but that isn't the case. The Nigerian Prince scam traces its roots as far back as the 1800s when it was known as the Spanish Prisoner scam.
All throughout history, humans have been trying to trick, manipulate, and take advantage of one another. The recent phenomena of internet-based social engineering attacks is merely a chapter in social engineering's long history. As ethical hackers, our role is not to trick people maliciously but to educate and train our coworkers and clients to identify malicious actors who use their psychological knowledge to further their own interests.
Scammers, hackers, and con artists have used social engineering for millennia, and the general idea hasn't changed much, but the actual implementations of the attacks are always evolving to take advantage of emerging technologies and to outpace the public's awareness of tactics. Here are two current examples of age-old attacks that are being updated with modern tech:
New Phishing Domain Names
The #1 type of social engineering attack is phishing. Phishing comes in many forms (such as spam emails), but a recent threat has emerged that will likely be a headache for cyber security professionals who try to educate their coworkers on identifying phishing attacks. This new threat is the creation of the .zip and .mov TLD (top-level domains) by Google, which means anyone can register domain names using this extension. I share SwiftOnSecurity, a popular cyber security Twitter commentator's, sentiment in calling this move "dumb."
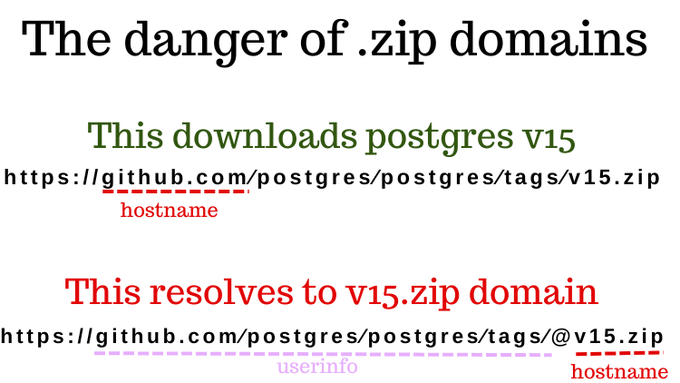
Let's look at an example of how this could be exploited in this infographic from Twitter user @hnasr:
What is the difference between the two urls?
one has an @ and one doesn't.But also the first downloads version 15 of postgres from GitHub and the second one resolves to v15 dot zip domain which can also downloads a zip file that sure doesn't have postgres in it.
You see,… pic.twitter.com/muGU1ruYdD
— Hussein Nasser (@hnasr) May 17, 2023
These new domains will make it even easier to hackers to create realistic-looking phishing URLs.
Vishing
Vishing is a term assigned to phishing-style attacks conducted on the phone using the attacker's voice.
Most people are fairly alert when it comes to random spam calls; however, when combined with information gained from reconnaissance, sophisticated attackers can be very believable. When used in combination with another attack adding a phone call into the mix can add credibility to an otherwise suspicious attack by making it seem more genuine rather than just a bot.
If you've been keeping up with tech news as of late, you've probably seen demos where a clip of someone speaking is fed into an AI-powered tool, and the user gets a custom text-to-speech tool. This is great for attackers. With enough digging, you can find a video of most people (especially well-known business people) on social media. If you want to go full James Bond, you could even directly obtain audio recordings. All you've got to do is get audio clips (doesn't matter how), and you can create a fake voice that sounds exactly like an authority figure which you could use to manipulate a subordinate into transferring money or other action via a vishing call. This kind of thing used to only live in the imaginations of movie and TV writers, but it's now a reality.
An interesting report published by the US HHS's Office of Information Security claims a form of vishing called "hybrid vishing" increased by 625% in Q2 of 2022. A hybrid vishing attack is typically characterized by a multistage vishing process where the attacker calls back or introduces other stages to their attack.
One common variation is where the attacker sends a phishing email that instructs the victim to call a number. Adding a phone call increases the perceived legitimacy of the email, making victims feel more comfortable with the attacker. From my own personal experiences, I know I've seen many companies say that they will never ask for passwords over the phone, but they obviously do ask for them through websites. If I get a call asking me to verify by opening a link sent to my email and to check my spam, I might feel comfortable enough to do it since that's an authentication method deployed by many legitimate companies.
Summary
Think of it like this. Both malicious hackers and ethical hackers follow a similar strategy for successfully meeting their objectives. To defend a system, cyber security professionals rely on a concept called "layered defense," where multiple security controls or defenses are layered on top of each other so that even if one fails or is breached, the overall system isn't completely exposed. Attackers can utilize the same concept by implementing a "layered attack" where multiple steps are combined to increase the chances of success. Just sending a phishing email or just making a vishing call isn't likely to succeed. But when combined into a hybrid vishing attack, the attacker has a much greater chance of success.
Just like a single attack is more likely to fail, so is a single defense. Defense strategies with single points of failure (while sometimes hard to avoid) are likely to eventually be breached. As information technology professionals, it's our job to identify weak points in the systems we design and develop so that we can add multiple layers of security between our protected assets and attack surfaces.
Social engineering attacks are as old as dirt, but that doesn't mean they're unstoppable. Using multiple layers of defenses and ensuring accountability is maintained helps mitigate the threat of social engineering to an organization. Like all cyber security threats, your organization will never be 100% safe, but investing resources and training into improving your odds could mean the difference between disaster and identifying an attack before it succeeds.









Top comments (0)