Overview
At AWS, cloud security is "job zero" task. Security is given high attention while developing AWS services and features. Network-level traffic filtration is one level of defense that can be used to protect your network and computers from security events. For all Amazon Virtual Private Cloud Infrastructure, Network Firewall is a highly available, managed solution that makes it simple to establish essential network security. To safeguard your virtual networks on AWS, it helps you to quickly create and manage stateful inspection, intrusion prevention and detection, and web filtering. With no additional customer investment in security infrastructure, Amazon Network Firewall automatically scales with your traffic to ensure high availability.
AWS Network Firewall consists of three essential parts.
- Rule Groups: It stores criteria for inspecting traffic and processing packets and traffic flows that match the inspection criteria.
- Policy: It specifies some policy-level behavior parameters as well as a reusable collection of stateless and stateful rule groups.
- Firewall: It enforces the firewall policy's inspection rules to the VPC that the rules are designed to defend. One firewall policy is necessary for each firewall. The firewall also specifies options for stateful traffic filtering and how to log information about your network traffic.
Deployment models for AWS Network Firewall
With AWS Network Firewall, various deployment types are possible. The appropriate model will rely on the requirements and use case. The following models are the most widely used:
- Distributed model: Amazon Network Firewall is deployed using a distributed deployment strategy in each VPC that needs security. Each VPC is independently secured, and VPC isolation reduces the explosion radius.
- Centralized AWS Network Firewall deployment model: In this for North-South (internet egress and ingress, on-premises) and/or East-West (VPC-to-VPC) traffic, a centralized VPC is used to deploy the AWS Network Firewall. AWS Transport Gateway is a requirement in this model. As a network hub, AWS Transit Gateway streamlines connectivity between VPCs.
Steps walkthrough
Under firewall creation, we will be creating Network Firewall Rule Group and Firewall policy first.
Create Firewall RuleGroup
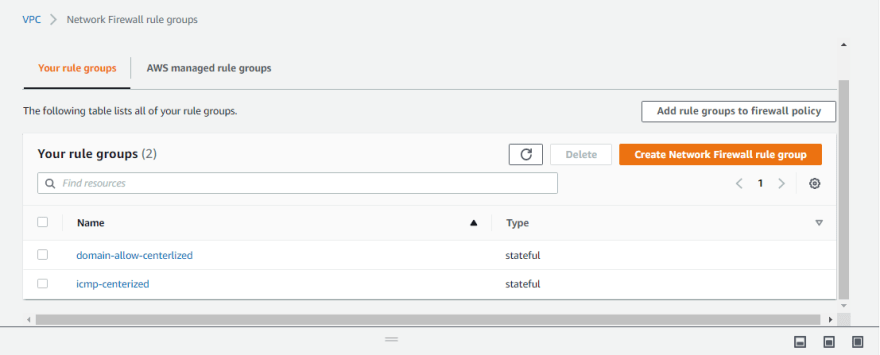
In this exercise, we will create two sets of rules:
- Alerting ICMP traffic
- Domain filter Go to VPC > Amazon Network Firewall > Network Firewall rule groups and click on Create Network Firewall rule group
Under Rule group type:
• Select Stateful rule group
• Specify Name
• Set Capacity to 100
• Choose 5-tuple from the Stateful rule group selections.

Choose ICMP as the protocol under "Add rule" and in action select alert; otherwise, leave everything else as is. Then, click "Add rule."

After adding the rule, scroll down and select Create stateful rule. Icmp-alert rule has successfully been created for group.

Create domain filter rule group
To filter/allow particular domains, a rule will now be created:
Go to VPC > Amazon Network Firewall > Network Firewall rule groups and click on Create Network Firewall rule group
Under Rule group type:
• Select Stateful rule group
• Specify Name
• Set Capacity to 100
• Choose Domain list under Stateful rule group options.

Under Domain list:
• Add .amazon.com
• Choose both HTTP and HTTPS under Protocols.
• Under Action select Allow
select Build stateful rule group

We have now created two rules.
To filter network traffic, you will construct firewall policies in this activity.
Go to VPC > Amazon Network Firewall > Firewall policies and click on Create firewall policy
Under Describe firewall policy:
Specify Name and click on Next
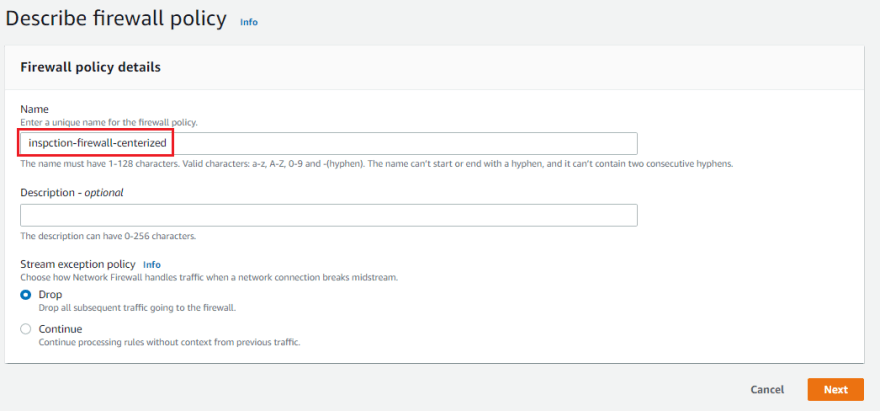
Under Add rule groups:
• Select for all packets, take the same step
• Under Action select Forward to stateful rule groups

Add rule groups by selecting both the domain-allow-centerlized and icmp-centerized rules under Stateful rule group.
Click Next, go over the information, and then select Build firewall policy.
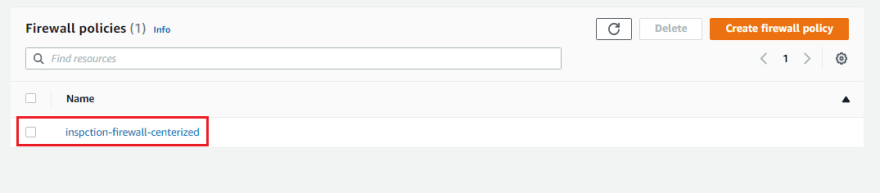
At this point we currently have one firewall policy created
We will build a firewall in this activity to inspect and filter network traffic.
Go to VPC > Amazon Network Firewall > Firewalls and click on Create firewall
Under Firewall details:
• Specify Name
• Under VPC, select inspection (VPC name, where the firewall
needs to be deployed)
• Under Availability Zone, select respice zones
• Under Subnet select firewall subnet and click on Next
Note: Right now we are going with one AZ deployment

Under Associated firewall policy:
• Select Associate an existing firewall policy and select inspction-firewall-centerlized
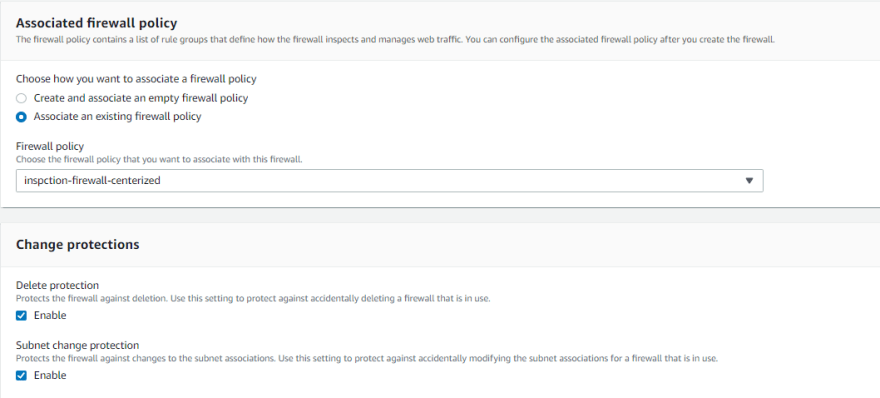
We currently have a Firewall that is provisioning. Be patient; it can take a while.
Configure Logging
Let's configure logging while your firewall is being provisioned:
Scroll down to Logging and click on Edit:

In the Firewall logging configuration edit box:
• For Log type select both Alert and flow
• Choose the CloudWatch log group under Log destination for alerts.
/network-firewall-centrlized
• Under Log destination for flows select CloudWatch log group and select /network-firewall-centrlized
and click Save:

At this point, we have a firewall in Ready state
Once firewall is in Ready state, we need to collect firewall endpoint id. These are the endpoints that will serve as targets for traffic directed at your firewall. Next, update the route table. Next, update the routing table adding the endpoint id with the respective availability zone route table.
You can inspect firewall logs after everything is linked and traffic is passing via the network firewall. The CloudWatch logs may take three to six minutes to update.
Reference link: https://catalog.workshops.aws/networkfirewall/en-US/setup/centralmodel/create-anfw/create-firewall-rule-group








Top comments (0)