Edited to include markdown. Originally posted here
I am making a digital transformation during this novel work-from-home (WFH) era due to a COVID-19 quarantine. Many of you are going through the same and distractions abound while sharing a workspace with housemates, children, and pets. Moreover, we have to contend with an increased risk to cybersecurity, given recent attacks on work-related software such as Slack and Zoom.
Despite exposing millions of accounts to attack, these companies provide
critical infrastructure for helping millions in quarantine be productive from
home. There is also an uptick in social engineering attacks that capitalize on
COVID-19 related business disruptions by attempting to deliver ransomware in phishing emails. Here are 10 tips I follow to provide immunity against digital viruses in my WFH environment.
1. Always use a camera cover and mute your microphone unless you are actively on a call.
While my encrypted connection is relatively secure, I am still leaving myself open to attack from third-party conferencing software without this precaution. Even if an attacker were to take over my Slack account or listen into my zoom calls, they would still not be able to access my microphone or video with a cam cover and a muted mic.

My laptop has a built-in cam cover but you can also use a sticker
2. Use a Virtual Machine (VM) for your personal use.
I do not store personal data (including web browsing) on my work laptop and instead use a free VM. Set up a separate, encrypted virtual machine to use as a personal environment for private searches and documents you want to have available on your work laptop. Never sign into personal accounts on your work computer while outside of this carefully siloed environment.
This is the encrypted VM that I use for personal files + browsing
3. Connect via VPN.
During work hours, my VPN is active and pings a private network in order to authenticate my entrance to Puppet portals. Most organizations use VPN connections to authenticate access for your work accounts through an encrypted connection to your work server. This prevents Internet Service Providers (ISPs) from accessing your private data.
4. Use HTTPS when web browsing.
Unless you have municipal broadband, you use an Internet Service Provider (such as Comcast). ISPs have access to your private data while web browsing (even through incognito mode) if you are not using an encrypted connection. If you are not connected to a VPN, make sure all websites you access are using HTTPS, which leverages SSL security. Pay attention if your browser warns you that you are getting an “invalid certificate”. This means that your connection is no longer encrypted.

Bail. Go “back to safety” when you see this!
5. Ensure you connect to a trusted, encrypted wi-fi network
If you are using Windows, your network should be configured with the “Public” Network Type setting checked. This ensures that network discoverability and “File and Print Sharing” are turned off. Otherwise, you expose your domain, machine name, mac address, and IP address for your local network. Also, your publicly shared folders will be available (potentially with read and write access) to anyone on the network. Moreover, there are many connections that are still vulnerable to port scanners and keyloggers that connect through certain wireless keyboard dongles. These attack vectors are especially common in apartment and condo complexes, where physical distances and networks are closer together.
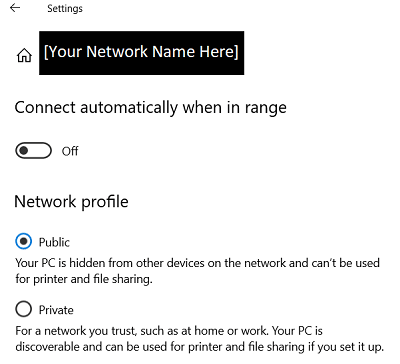
These are my recommended network settings (on Windows)
6. Turn off scripts when web browsing.
Install the plugin “NoScript”. Then, whitelist acceptable domain names that are relevant to your work. Scripting is a common attack vector that uses scripts to pull data from your computer like your clipboard or your browser’s cache and cookies. The malicious actor could potentially gain access to your login credentials (through cookies) to other secured websites.
I use Firefox with NoScript on my add-ons
7. Create strong passwords (with two-step authentication)
Try to use “pass phrases” that are easy to remember (i.e. I7oveD1sney7and!). This gives you length and variety to your password so that it is robust enough to be secure while still easy enough to remember. If you use two-step verification, attackers would not be able to log into your accounts, even if they have your password…so set that up!
8. Don’t install executable files
…from un-trusted publishers. They are probably keyloggers or computer viruses. No, “watch-cute-animals-now.exe” is not worth the risk. Also, keep user account control enabled (in Windows) so you have to authorize all installations.
9. Check the domain name
Try to not click on random links and make sure you are not on “mellsfargo.com” or other similar sites. Double-check your entry for spelling errors when you type in URLs such as: “https://relay.sh” (where I work).
10. Check your firewall and anti-virus settings
While I do not feel the need to run anti-virus software on my linux VM, most of you lovely readers are probably using Windows. Windows Defender is free and the only anti-virus software you need. Firewall settings come pre-configured too! For the Apple users: You are in luck because there aren’t as many viruses for macs. However, let me point you to this PC Magazine article to learn more. Please remember that virus scanners are only useful if you run manual scans and keep up with updates.
Conclusion
Hopefully this guide serves to help quarantine your computer from digital viruses during your WFH transition. Please comment and leave some of your own tips!







Top comments (5)
Hey there, you should consider sharing the article you wrote on Medium in full here on DEV. It seems like a cool post. 🙂
You have the ability to add a canonical link back to the original source if you do decide to share it here.
Sure - This is my first DEV post on a baby account. How does one do that while preserving formatting and images? Maybe I can add a TL;DR post with just the 10 tips.
No worries!
I think a Tl;DR post would work great with this post. 😀
However, if you set up publishing from RSS then you can import posts onto DEV. To be perfectly honest, sometimes goofy stuff does happen with formatting and images when importing, but it's better than having to start fresh. I've also used this site for converting html to markdown, which might be helpful to you!
Anyway, I appreciate ya hitting me back here. Hopefully this "baby account" will become a regular thing for ya! It seems like you have some really cool posts to share here.
Hope ya dig DEV and let me know if you have any questions!
Thanks for the suggestions - I just edited this to include the markdown. Yeah - the formatting gets funky but I just made some changes to fix that. First post on DEV so I appreciate the patience!
Woot! It looks great! Thanks for sharing these tips.