Email/Password
Reset password
Check for session tokens in the URL:
http://enum.thm/labs/predictable_tokens/reset_password.php?token=123
In the example above, we can see that the token is 3 digits. We can capture this request to Burp Suite, send it to intruder, highlighting the 123.
Then we generate a list of tokens.
crunch 3 3 -o otp.txt -t %%% -s 100 -e 200
-
3: minimum digits -
3: maximum digits -
-o otp.txt: output file -
-t %%%: output format -
-s 100: start from -
-e 200: ends at
Using Sniper Attack and Simple List payload, we can start the attack.
We then check for the longest content length, taking a peek at its response.
Basic Authentication
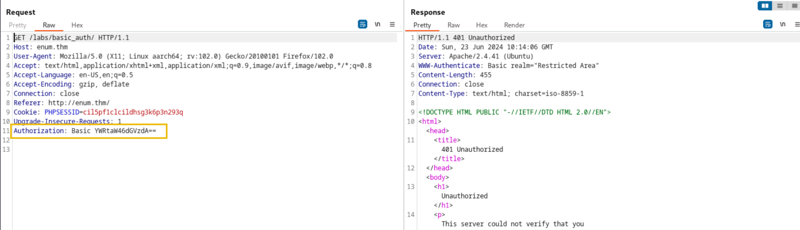
Input username and password, capture the request in Burp Suite, check out encoded credentials. We have an example of credentials encoded with Base64.
In this example the encoded credentials are under the Authorization: Basic <credentials>
As we decode it, we get the format username:password.
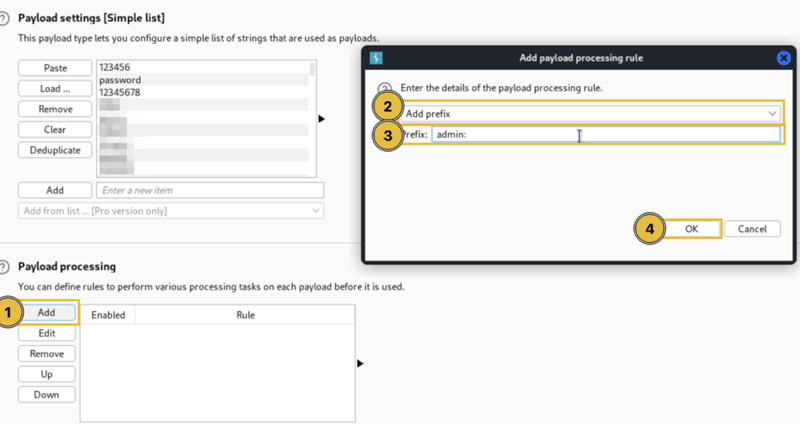
We can instead brute force our way in using 500-worst-passwords or any other password list.
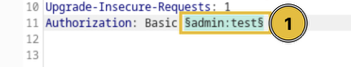
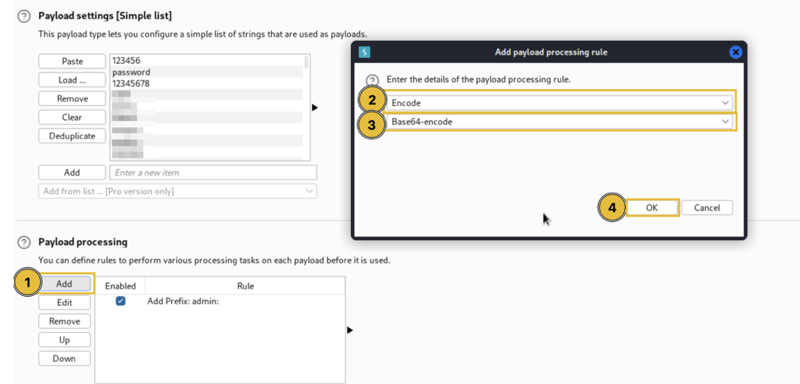
We add a prefix rule as the username.
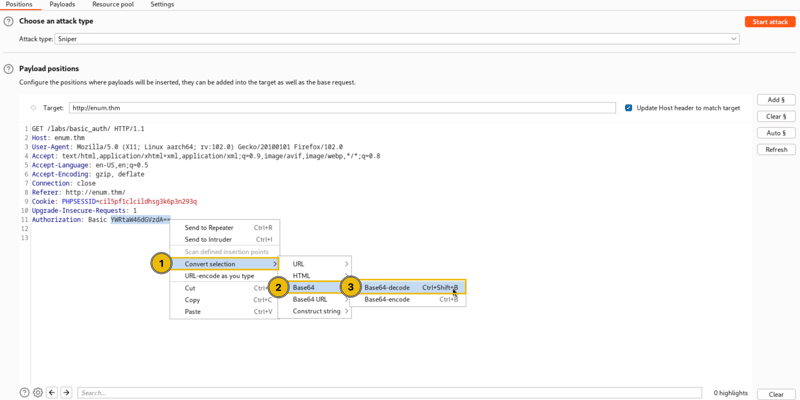
We also add the Base64 encode rule as the credentials are encoded with Base64 and sent to the server.
We should also remove the character "=" (equal sign) from the encoding because base64 uses "=" for padding.
Start the attack and look out for the request with valid status code (200-399) and check its response.
Relics of the Past
Using Wayback Machine, we can check past versions of sites, perhaps old unremoved directories which can act as a backdoor into the website.
We can install it onto our machine here.
git clone https://github.com/tomnomnom/waybackurlscd waybackurlssudo apt install golang-go -ygo build
Example output:
user@tryhackme $ ./waybackurls tryhackme.com
[-- snip --]
https://tryhackme.com/.well-known/ai-plugin.json
https://tryhackme.com/.well-known/assetlinks.json
https://tryhackme.com/.well-known/dnt-policy.txt
https://tryhackme.com/.well-known/gpc.json
https://tryhackme.com/.well-known/nodeinfo
https://tryhackme.com/.well-known/openid-configuration
https://tryhackme.com/.well-known/security.txt
https://tryhackme.com/.well-known/trust.txt
[-- snip --]
By crafting specific search queries, known as Google Dorks, you can find information that wasn’t meant to be public. These queries can pull up everything from exposed administrative directories to logs containing passwords and indices of sensitive directories. For example:
- To find administrative panels:
site:example.com inurl:admin - To unearth log files with passwords:
filetype:log "password" site:example.com - To discover backup directories:
intitle:"index of" "backup" site:example.com








Top comments (0)