Flag 1
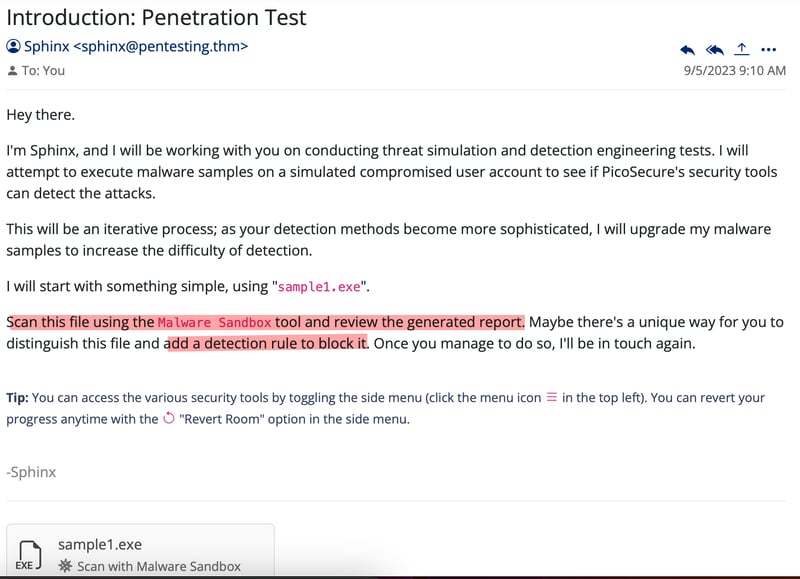
Once entering the room, we are greeted with an email as follows.
Objective:
- Scan the file
- Block it
So with that said, just submit it for analysis by clicking on the file, then "Submit for Analysis".
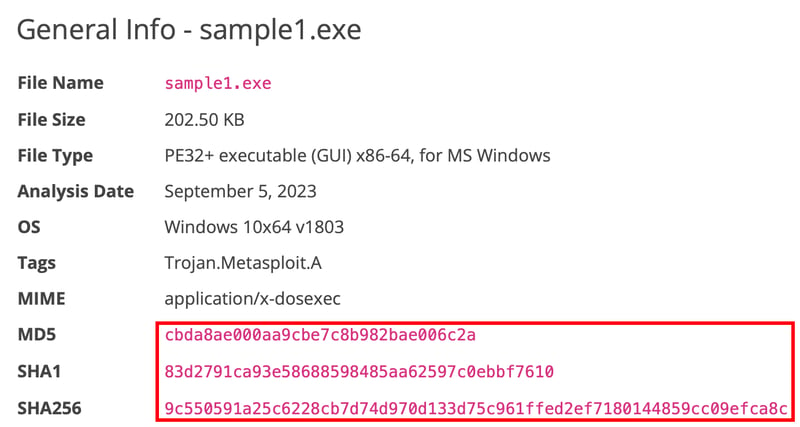
Once the scanning is complete, a report will be generated. We then just copy one of the hashes and proceed to scan it, by navigating to the burger on the left and go to Manage Hashes.
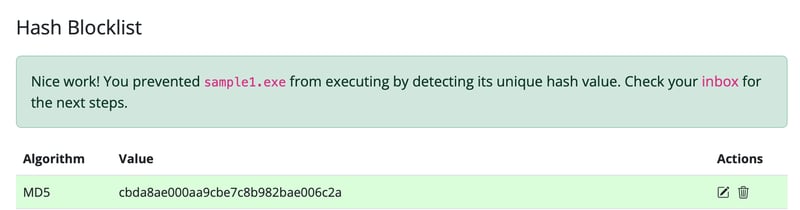
From here we just paste any of the hashes we copied, make sure to choose the correct hash type too.
After that, we will recieve an email, which contains flag 1.
Flag 2
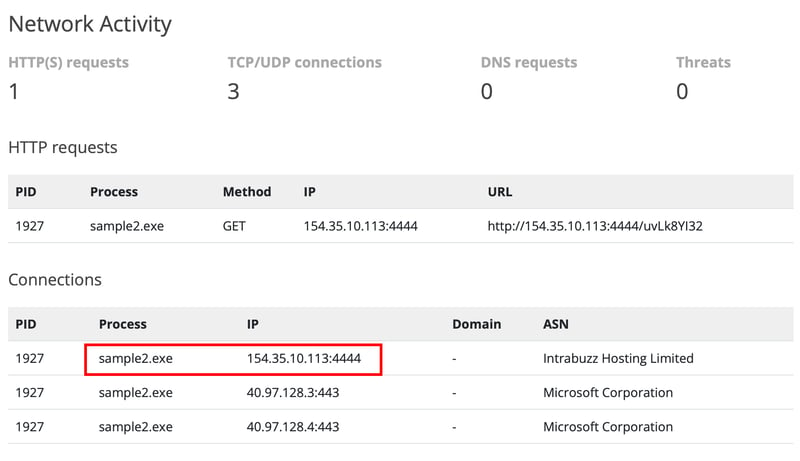
Now we repeat the previous steps to scan sample2.exe. This time it is different as suggested in the email, as we can detect network activity.
Network activity listening on port 4444 is always suspicious, as it is the default port for Metasploit framework. It is also running a request using HTTP instead of HTTPS, which is another valueable observation.
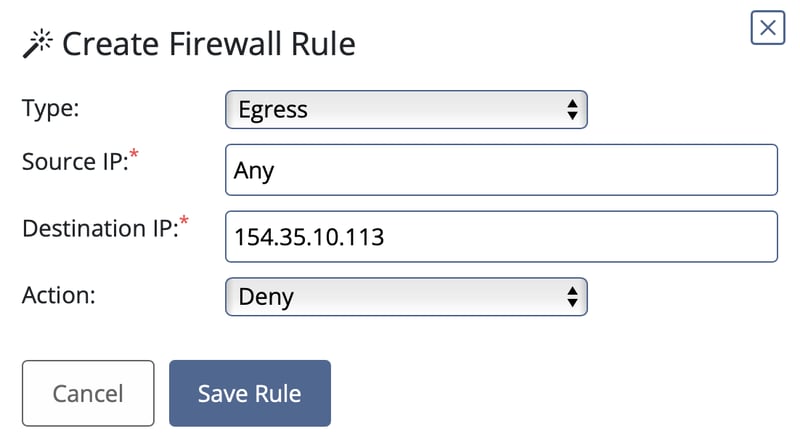
We set type to "Egress" as the HTTP request of http://154.35.10.113:4444/uvLk8YI32 redirects us to access the external resource from that specific IP.
As we want to deny all traffic to that malicious IP, we set so that Any IP having contact with that malicious IP as Denied.
And with that we got our second flag.
Flag 3
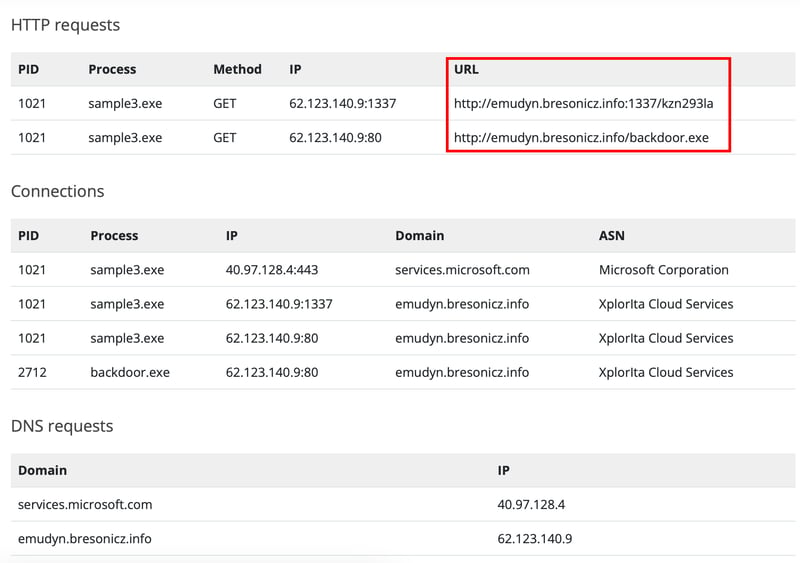
After the report is generated upon scanning sample3.exe, we can see that the domain HTTP request to emudyn.bresonicz.info is trying to let us access a resource called backdoor.exe.
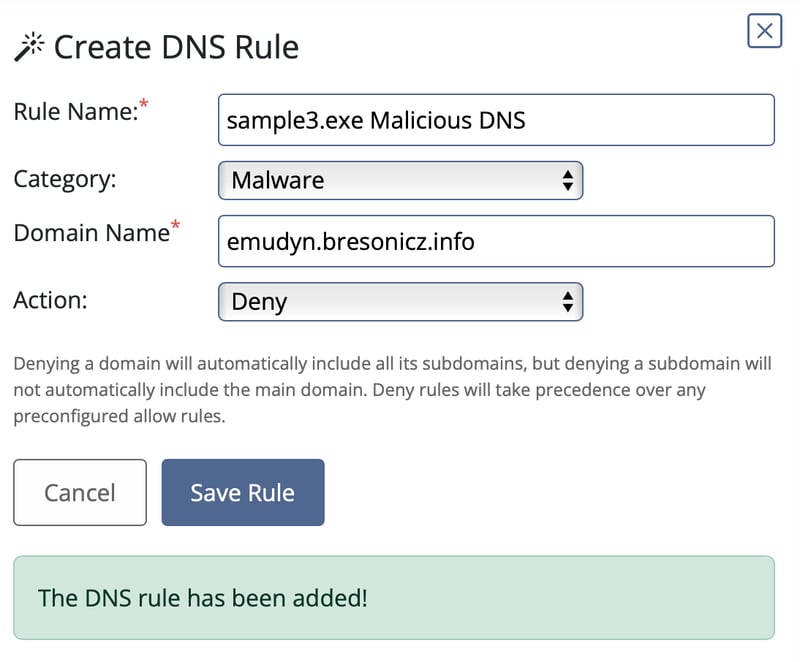
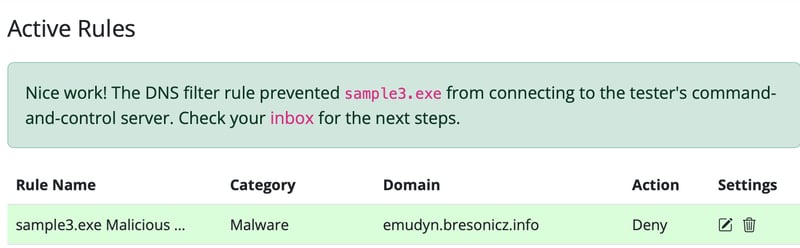
So with that we just create a DNS rule to block it to prevent any interactions with that domain again.
And flag 3.
Flag 4
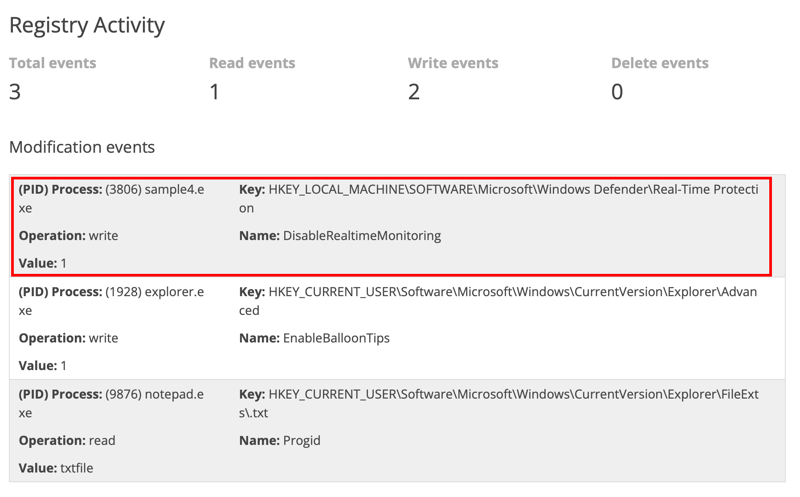
Looking into the report generated, we can see that the attacker managed to disable firewall real time monitoring on our system with its malware.
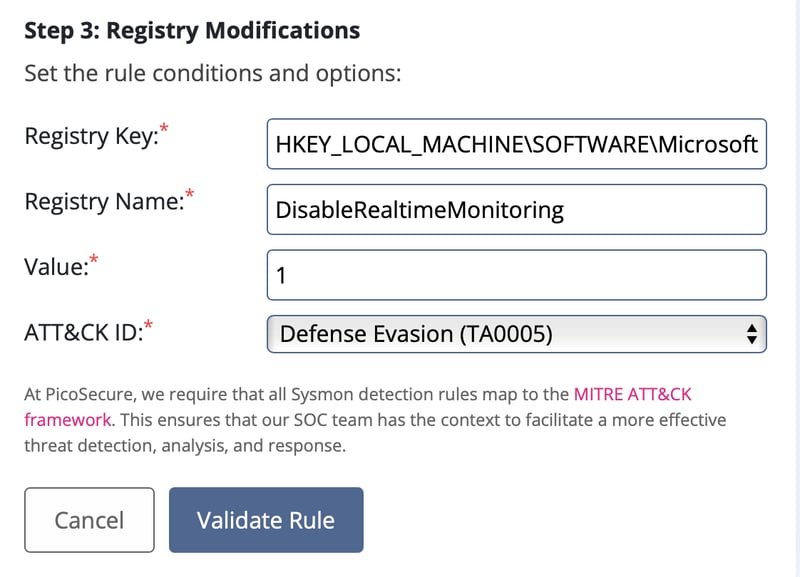
With this event, we can go to Sigma Rule Builder, select Sysmon Event Logs, and Registry Modifications.
We then just key in all the details regarding the registry modified. As this is an Defense Evasion technique, we select that to complete our sigma rule.
And there is flag 4.
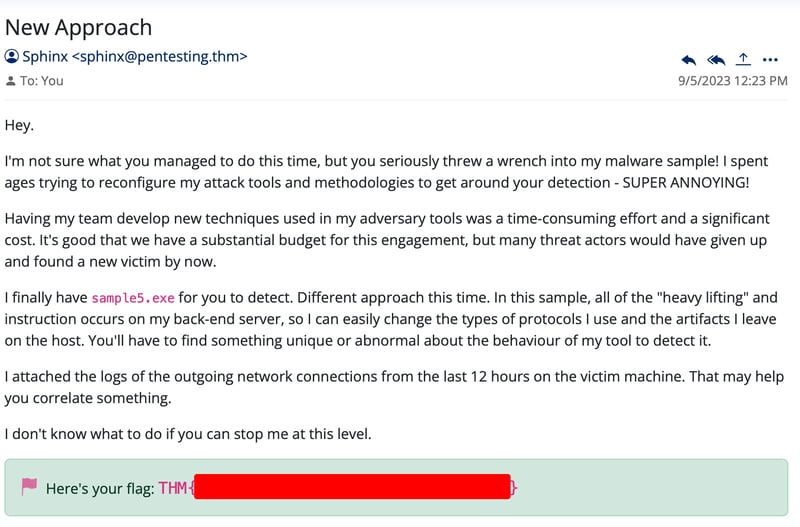
Flag 5
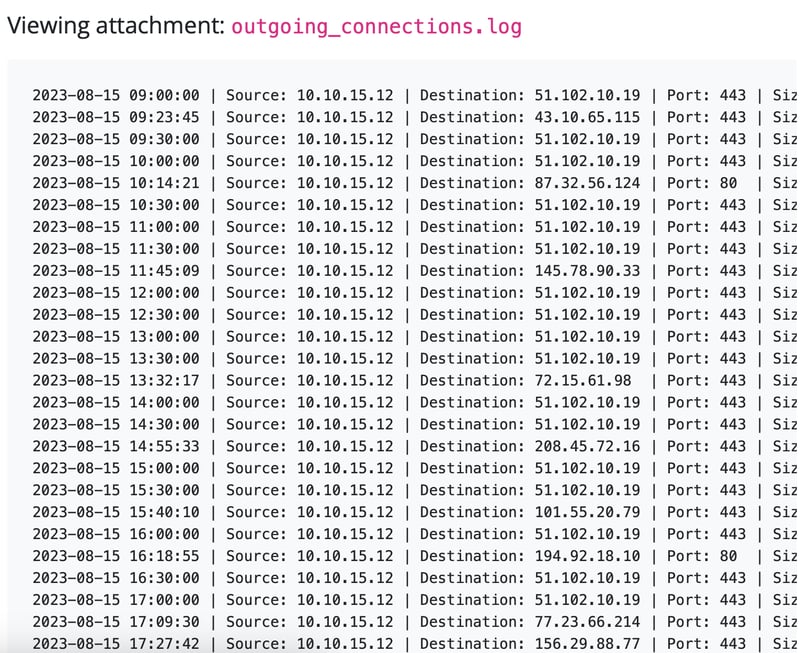
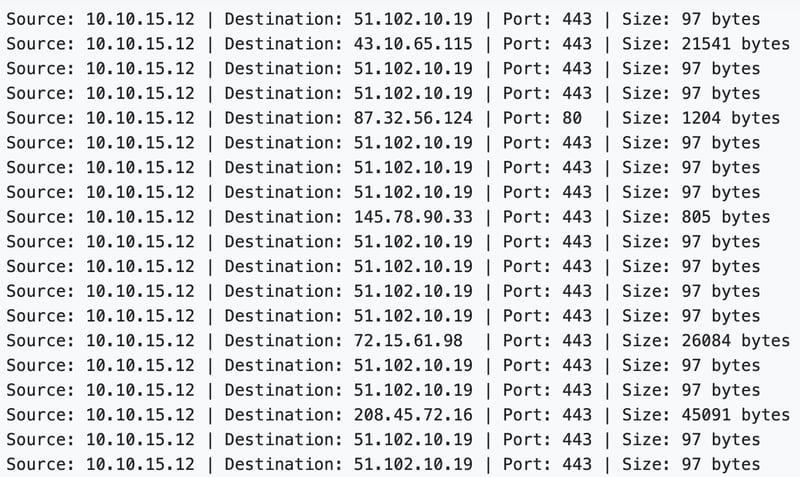
In the email, he mentioned on the file attached as the logs of the outgoing network connections from the last 12 hours on the victim machine.
We see that frequent request has been made towards various IPs.
The red flag is the size of information sent. Some are consistently the same size, specifically 97 bytes.
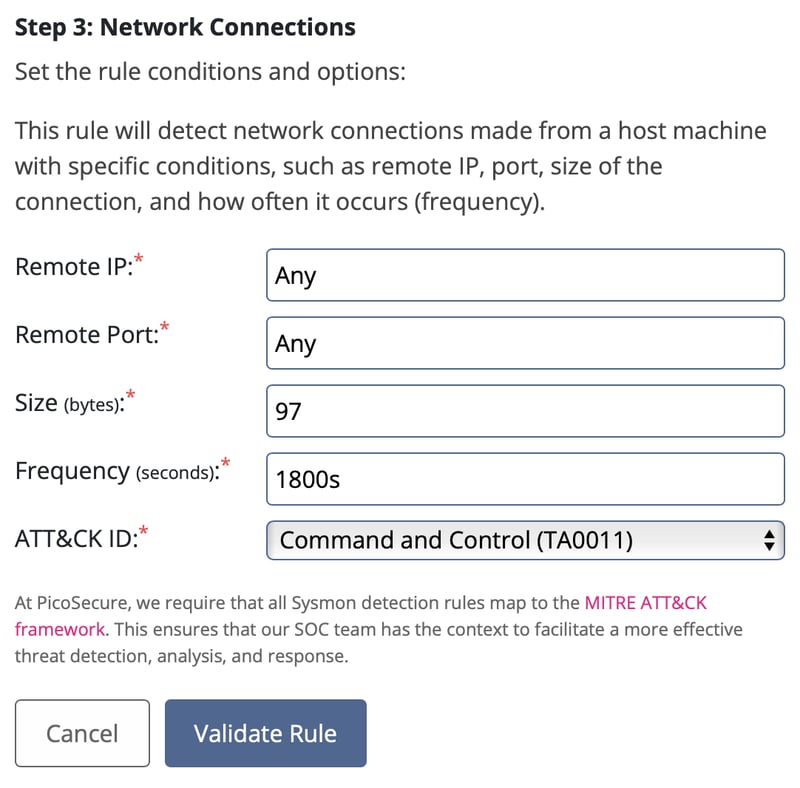
After knowing this, we just navigate to Sigma Rules -> Sysmon Event Logs -> Network Connections
The reason why blocking the sole IP may not work is because attacker can change their IP easily, so stopping it that way may not be effective.
And flag 5 is attched to the email.
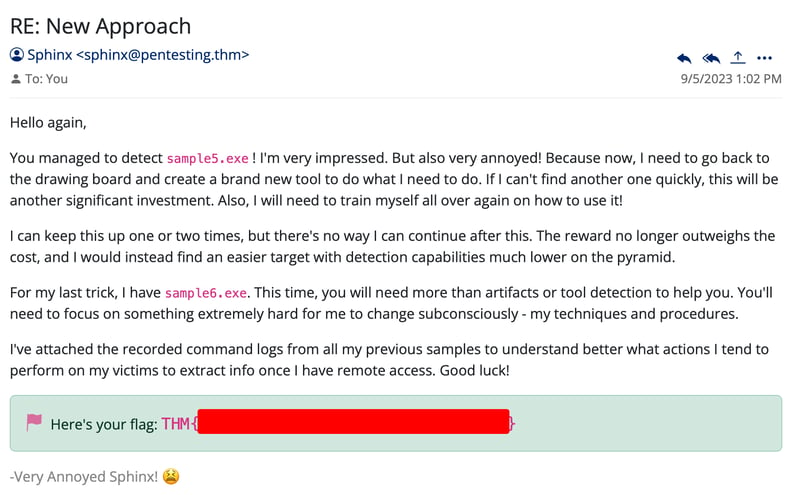
Flag 6
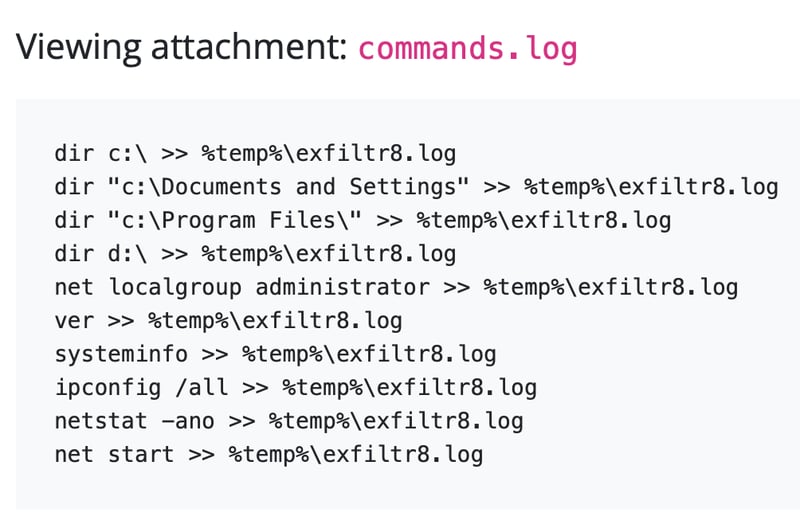
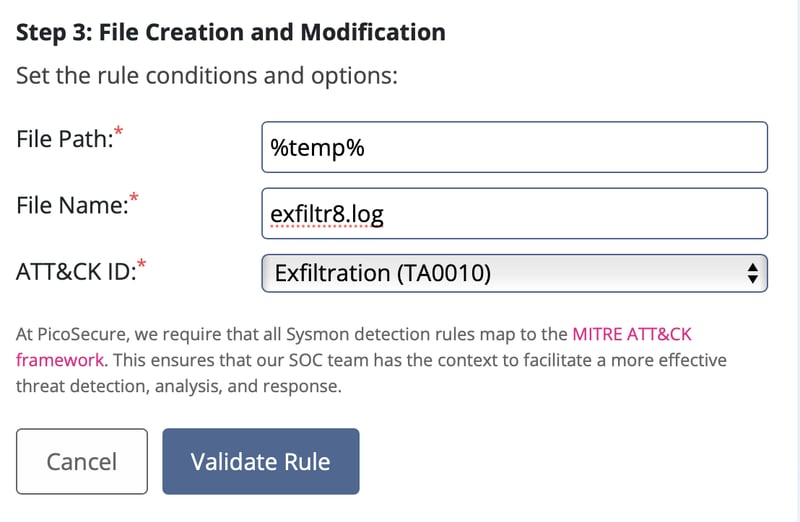
The new email has commands.log attached, which shows a file with the following contents.
We can see that the attacker is exflitrating data from the victim machine, appending them onto a file disguised as a log file.
Following the path of the log file, we just block the file creation and modification to prevent further compromise.
And flag 6 will be here.







Top comments (0)