What are Cyber Attacks ?
A cyber attack is any type of offensive action that targets a computer system, infrastructure, computer networks, or professional computer devices by using various methods to steal or destroy data or information systems.
I know it is quite difficult to understand this in the first attempt.
Let me break down into simple words.
A cyber attack is a malicious and deliberate attempt by an individual or organization to breach the information system of another individual or organization.
Usually, the attacker seeks some type of benefit from disrupting the victims' network.
A cyberattack is also known as a Computer Network Attack (CNA), if you have ever studied a famous battle in history, you will know that " No Two are exactly alike. "
Still, there are similar strategies and tactics often used in battle because they are time-proven to be effective.
Similarly, when a criminal is trying to hack an organization, they won't reinvent the wheel unless they absolutely have to.
They will draw upon common types of hacking techniques that are known to be highly effective, such as malware, phishing or cross sites scripting, etc...
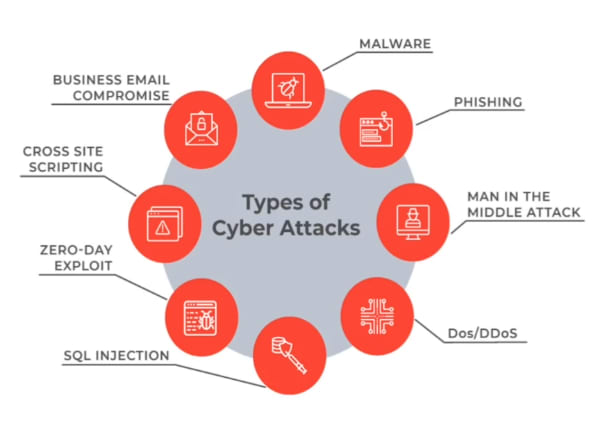
Some common Cyber Attacks
Here, we will discuss some of the common types of cyber attacks such as :
- Malware Attacks
- Phishing Attacks
- Man in the Middle Attack
- Dos/DDos Attacks
- SQL Injection
- Cross-site Scripting
- Business email compromise
We will discuss each type of cyber attack briefly.
1. Malware Attacks :
If you have ever seen antivirus alerts pop up on your computer
screen or if you have mistakenly clipped a malicious e-mail attachment, then you have had a close call with malware.
Attackers love to use malware to gain a foothold in a user's computer and consequently the office they work in because it can be very effective.
Malware refers to various forms of harmful software such as viruses, ransomware, and Trojans.
Once malware is in your computer, it can break all shots of havoc. From taking control of your machine to monitoring your actions and keystrokes to silently send all shorts of confidential data from your computer or network to the attackers' computer network.
Attackers will use a variety of methods to get malware into your computer, but at some stage, it often requires a user to take any action to install the malware.
This action can include clicking a link to download a file or opening an attachment that may look no harmless, like a word document or PDF attachment but actually, it has malware installed hidden.
2. Phishing Attacks :
Of course, there are chances that you would not just open a random
attachment or click on a link in any e-mail that comes your way. There has to be a compelling reason for you to take action. Attackers know these too.
When an attacker wants you to install malware or divulge sensitive information. They often turn to phish tactics or pretending to be someone or something else to get you to take any action that you normally would not.
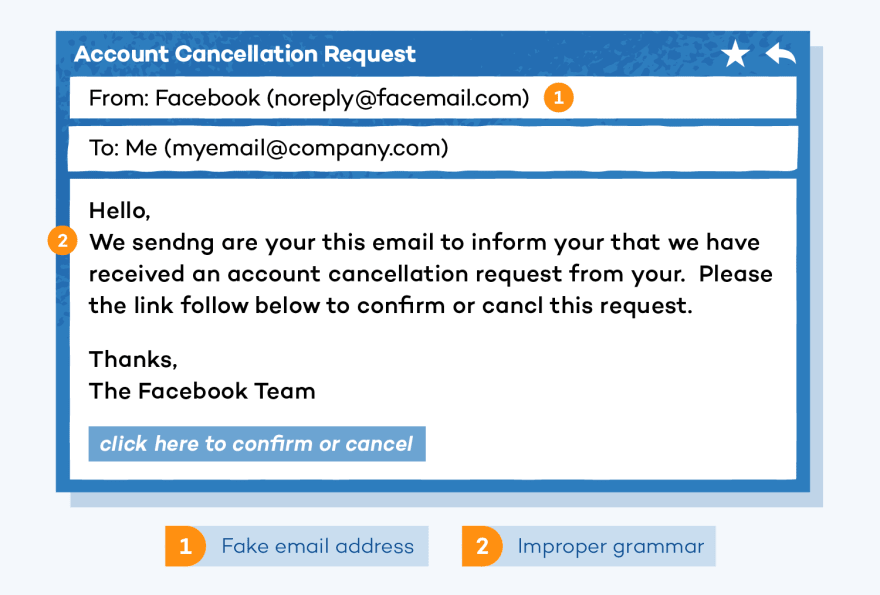
Since they rely on human curiosity and impulse phishing attacks can be difficult to stop. In a phishing attack, an attacker may send you an email that appeared to be from someone you trust, like your boss or a company you do business with. The email will seem legitimate and it will have some urgency to it.
For example, attackers may send you an email about a fraudulent activity that has been detected on your social media account or any other platform. In the email, there will be an attachment to open or a link to click on.
Upon opening the malicious attachment, you will thereby install the malware on your computer. If you click the link, it may send you to a legitimate-looking website that asks for you to log in to access the important file.
This legitimate-looking website is actually a trap used to capture your credential when you try to log in. To combat phishing attempts, understanding the importance of verifying email-sender attachments and links is very essential.
3. Man in the Middle Attack :
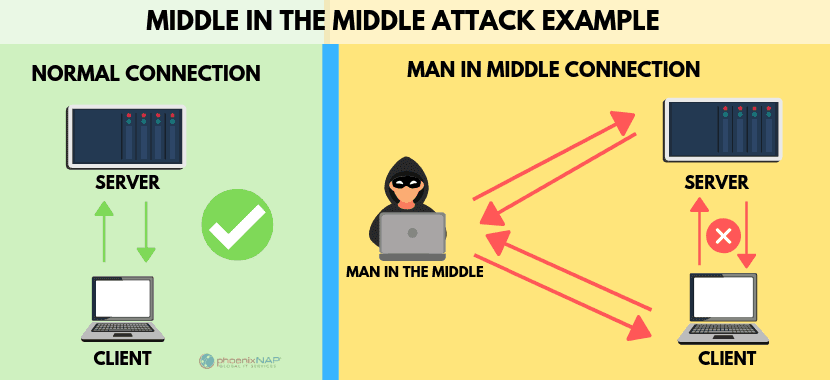
Now, let's talk about session hijacking and man in the middle attack. When you are connected to the Internet, your computer has a lot of small back and front transactions with servers around the world, letting them know who you are and what type of specific websites or services you are requesting.
If everything goes as it should, the Web server should respond to your request by giving you the information you are accessing. This process or session happens whether you are simply browsing or when you are logging into a website with your username and password.
The session between your computer and the remote web server is given a unique session ID which should stay private between the two parties. However, an attacker can hijack the session by capturing the session ID and posing as the computer making a request which allows them to log in as an unsuspecting user and gain access to unauthorized information on the Web server.
There are numbers of methods an attacker can use to steal the session ID, for example, a cross-site scripting attack can also be used to hijack a session I.D. An attacker can also opt to hijack the session to insert themselves between the requesting computer and the remote server by pretending to be the other party in the session.
This allows them to encrypt information in both directions. This method is commonly called A Man in the middle attack.
A man in the middle attack is a general term for when an attacker positions himself in a conversation between a user and application by making it appear as if a normal exchange of information is underway. The goal of an attack is to steal personal information such as login credentials, account details, and credit card numbers, etc ...
Targets are typically the users of financial application sites, businesses, e-commerce sites, and other websites where logging in are required. Information obtained during an attack could be used for many purposes, including identity theft, unapproved fund transfer, or an illicit password change.
Broadly speaking, a man in the Middle attack is the equivalent of a mailman opening your bank statement, writing down your account details, and then reselling the envelope and delivering it to your door.
There are some practical tips to prevent the man in the middle attack, such as
a. Avoid Wi-Fi connections that are not password protected.
b. The next one is, to log out immediately from a secure application when it is not in use.
c. The third one, Avoid using public networks such as coffee shops and hotel WIFI when conducting sensitive transactions, etc...
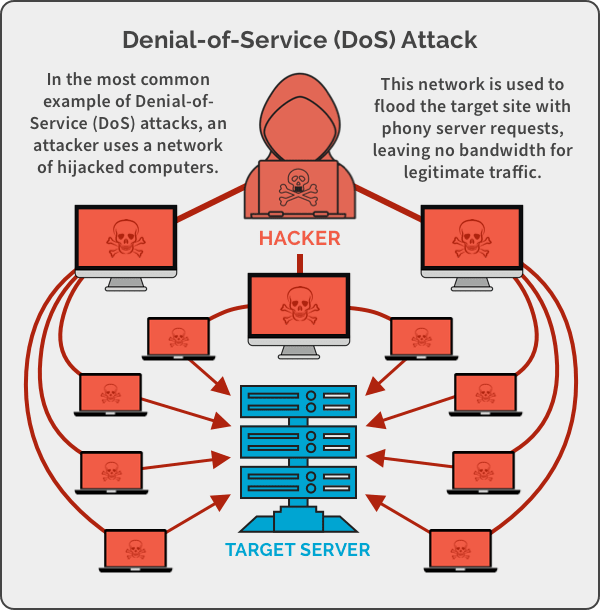
4. Dos/DDos Attacks :
I. Denial of service (DoS) – Attacker will try to prevent the normal use of server or application or database or network or communication facilities.
II. Distributed DoS attack – Attack is done from multiple and various systems at the same time. This is prevented by blocking an IP address from which you get too many requests.
5. SQL Injection :
Now let's discuss SQL injection Attack. As known, SQL ( also pronounced as sequel) is a programming language that is used to communicate with database. Many of the servers that store critical data for websites and services use SQL to manage the data in their database.
SQL injection attack specifically targets this kind of server using malicious codes to get the server to extract information. This is especially problematic if the server stores private customer information from the websites, such as credit card numbers, usernames, and passwords like other credentials or other personally identifiable information which are tempting and lucrative targets for an attacker.
A SQL injection attack works by exploiting any one of the known SQL vulnerabilities that allow the SQL server to run malicious codes.
For example, if a SQL server is vulnerable to an injection attack, it may be possible for an attacker to go to a website search box and type in code that would force these sites SQL server to dump all of its stored private data for this site.
6. Cross-site Scripting :
Now we will discuss cross-site scripting attacks. In an SQL injection attack, an attacker goes after a vulnerable website to target its stored data such as user credentials or sensitive financial data.
But if an attacker would rather directly target a Web site user, they may opt for a cross-site scripting attack. Similar to SQL injection attack, this attack also involves injecting malicious code into a website, but in this case, the website itself is not being attacked.
Instead, the malicious code the attacker has injected only runs in the user's browser when they visit the attack website. And it goes after the visitor directly, not the website. One of the most common ways an attacker can deploy a cross-site scripting attack is by injecting malicious code into a comment or a script that could automatically run.
For example, they could embed a link to a malicious JavaScript in a comment on a blog. Cross-site scripting attacks can significantly damage a website for reputation by placing the user's information at risk without any indication that anything malicious even occurred. Any sensitive information a user sent to a site such as their credential, credit card information, or other private data can be hijacked via cross-site scripting without the website's owners realized that there was even a problem in the first place.
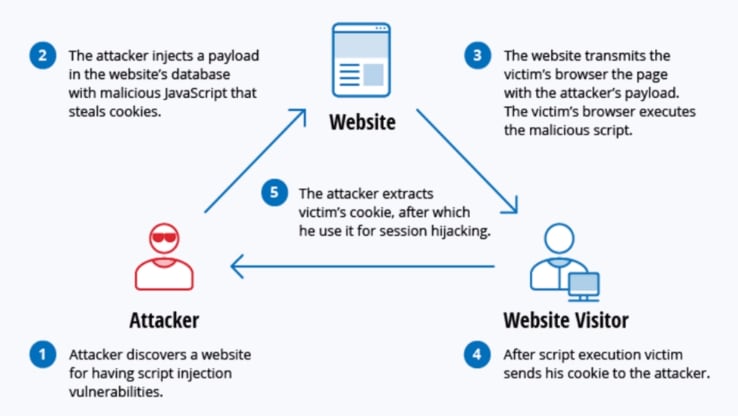
You can easily understand a Cross-site Scripting attack by this below image mentioned in five simple steps.
7. Business e-mail compromise :
Now we will discuss the Business email compromise attack. A business email compromises when an attacker hacks into a corporate email account and impersonates the real owner to defraud the company, its customer, partners, and employees into sending money or sensitive data to the attackers' account. A business email compromise is also a type of man in the middle attack.
This is derived from the man in the middle attack where two parties think that they are talking to each other directly, but in reality, an attacker is listening in and possibly altering the communication.
The attacker will try to gain access to the executive's email account. To remain undetected, He/She might use inbox rules or change the reply-to address so that when the scam is executed, the executive will not be alert. Another trick is to create an email with a spoofed domain.
For example, the attacker might use john.smith@samp1e.com instead of john.smith@sample.com {OR} use john.smith@believeme.com instead of john.smith@beleiveme.com. If you do not pay close attention, it is easy to get fooled by this slight difference.
One of the most famous spoofed domain tricks ever was PayPal.com, where the attacker changed the spelling from PayPa1.com.
How to stay away ?
Note: These are not the solutions to completely escape from these attacks, but it will help you up to some extent.
" PREVENTION IS BETTER THAN CURE "
- Use an Internet Security Suite.
- Use Strong Passwords.
- Keep Your Software Up-to-Date.
- Avoid Identity Theft.
- Always Browse in Anonymous Mode.
- Use End-to-End Encrypted Messaging Apps.
- Use a VPN to Protect Yourself From Service Providers.
- Stay Private on Wi-Fi Networks.
- Stay away from clicking/opening unknown files/links.
- Take appropriate actions if you have been a Victim.
Written by - Gudi Varaprasad












Top comments (1)
Excellent and well articulated blog! 👏👍