The recently published “OWASP API security top 10” report analyzes the anti-patterns that lead to vulnerabilities and security risks in APIs. In this 10 part series, we introduce these API anti-patterns. Every API professional should know about these anti-patterns. In this blog post, we focus on “API security misconfiguration”.
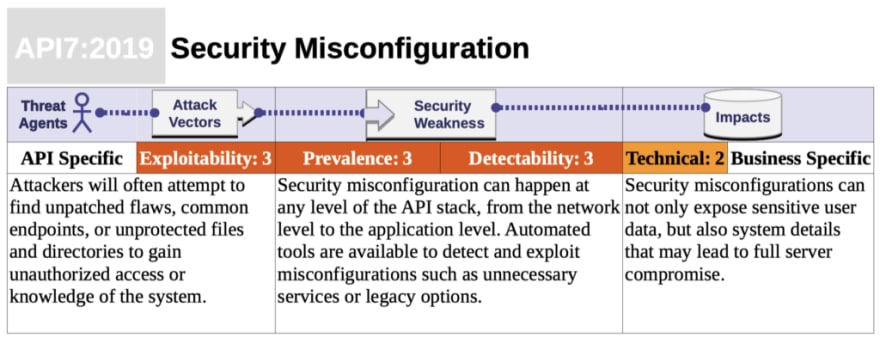 API security anti-pattern for Security Misconfiguration
API security anti-pattern for Security Misconfiguration
Security misconfiguration is commonly a result of insecure default configurations, incomplete or ad-hoc configurations, open cloud storage, misconfigured HTTP headers, unnecessary HTTP methods, permissive Cross-Origin resource sharing (CORS), and verbose error messages containing sensitive information.
The good thing is, that it is relatively easy to fix security misconfiguration and considerably improve the API security as a result.
Want to learn more?
- Part 1 Broken Object Level Authorization
- Part 2 Broken User Authentication
- Part 3 Excessive Data Exposure
- Part 4 Lack of Resources & Rate Limiting
- Part 5 Broken Function Level Authorization
- Part 6 Mass Assignment
- Part 7 Security Misconfiguration
Check out the complete OWASP API security paper. To secure access to your APIs, learn more about the OAuth in the OAuth Book, or the OAuth Course. To provide and use identity data in apps and APIs, learn more about OpenID Connect in the OpenID Connect Book, or the OpenID Connect Course.






Top comments (0)