Welcome Everybody! It's been quite a while since I was off from writing my security discoveries on this blog. I was minimally occupied nowadays learning some development stuff, so I can barely get time to write here. In that time I posted my video proof of concept on my YouTube channel. After Google, WhatsApp, Sony, Adobe and Intel this time I've established a security flaw, not in Microsoft itself but rather one of the famous acquisitions of Microsoft which is Minecraft.
"Minecraft is a computer game designed in 2009 by a Swedish programmer Markus Persson. He claims it now has over 100 million registered users". You might be wondering, did I find a security defect in the Minecraft game, isn't that so? No, I've established Security weakness in one of the subdomain of Minecraft which is education.minecraft.net.
Alot of researchers and friends out there were asking to reveal my report content. I posted underneath a screenshot of my report also. I hope you gain something from it.
In case you're from a security background you'll understand that report without pushing your mind. I'll clarify these terms additionally as we go through them.
IDOR(Insecure Direct Object References) In Microsoft(Minecraft)
Insecure Direct Object References occur when an application provides direct access to objects based on user-supplied input. As a result of this vulnerability attackers can bypass authorization and access resources in the system directly, for example database records or files.
On 4th October 2017, I began testing education.minecraft.net and right away I found IDOR vulnerability in lessons draft page. This flaw allows me to edit or modify anybody lessons draft page from my side without letting them know.
This weakness allows an attacker to change the content of any user's save lessons without any authentication or authorization. He could delete and change the content of Lessons draft page.
How I was able to produce this Vulnerability
This vulnerability allows an attacker to change the content of any users save lessons without any authentication or authorization.It was observed that by simply changing the value of create-lesson?edit=[ID] in the URL, it is possible to edit and delete a lesson for the user associated with that particular lesson ID.
- Suppose I have two accounts one is open in Chrome and other in Firefox.
- Presently I navigate to my Lessons and I made and saved a lesson that is located at
- https://education.minecraft.net/make lesson?edit=950077
- Same process I have done with my other account that is on other browser and this time I got
- another lesson ID that is https://education.minecraft.net/make lesson?edit=949958
- Now in both above links there is only difference of Lesson ID.
- I opened first link in second browser(Not the account in which lessons is created) and all I see the
- The content of other account's lessons is visible to me and I can undoubtedly modify it, Delete it, Change it, Submit it for review and whatever the attacker needs to perform.
Take a look at this video proof of concept for more clear understanding.
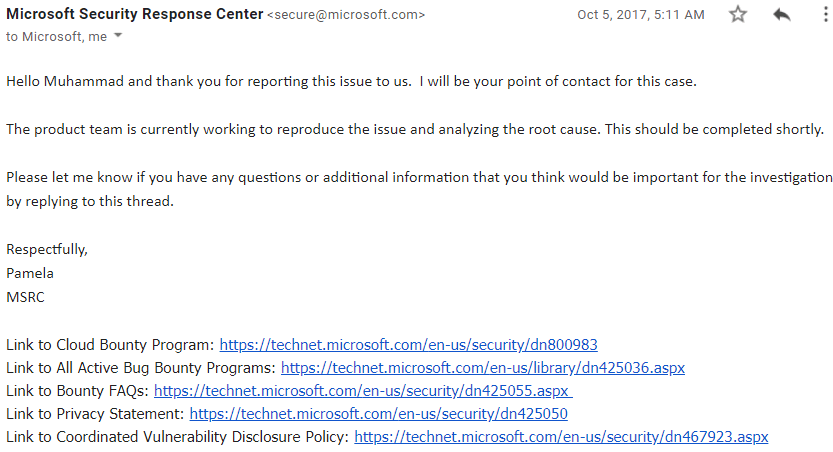
I reported this security imperfection to Microsoft as MSRC handles the security of all of the Microsoft services.
After reporting this security issue to Microsoft they answered me back following the multi week.
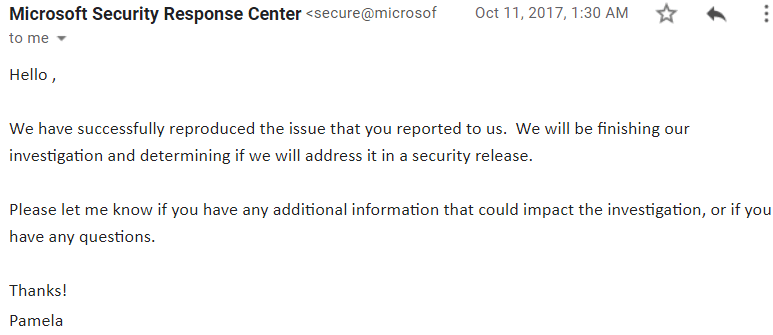
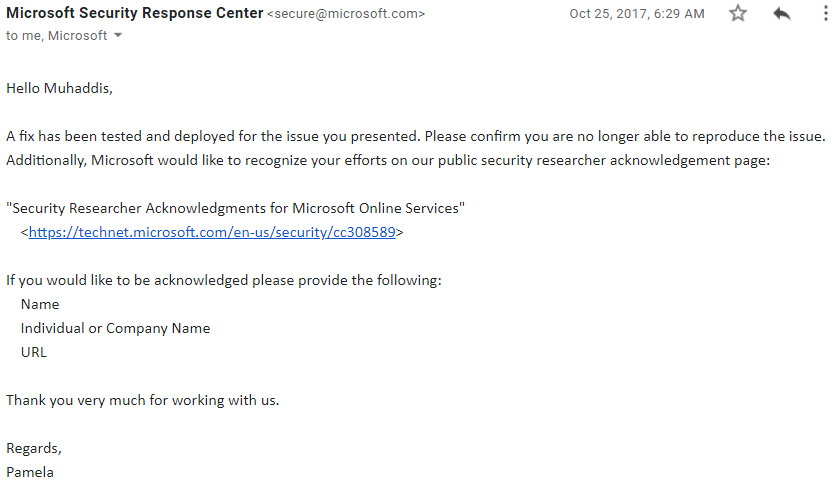
Following a couple of days they tried and settled that issue and asked me for confirmation from my side whether it's producible or not. I tried that and it looks fixed from my side. They offered me to be mentioned in their security researcher hall of fame. I provided them all of my details but unfortunately that page never updated with my name. I continued mailing them and reached them out of Microsoft too yet lamentably no response.
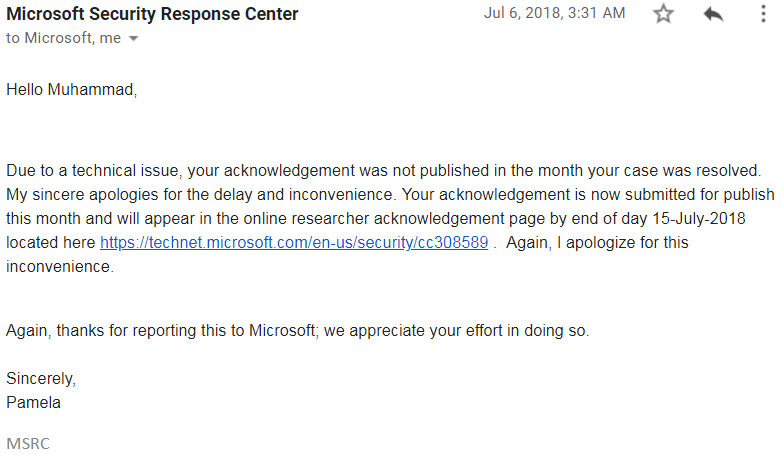
After exactly nine months they responded that there was some technical issue and that is the reason I was not able to get featured in that security hall of fame.
Impact
IDOR is considered as a serious security flaw and its Impact can prompt break data of millions of users of the application. One researcher could delete the account of every user in this site with the same flaw with no further validation. In case you're an application engineer and perusing this I'll very prescribe you to investigate these sort of issues. Your little shortcoming can prompt extraordinary loss.
Following nine months I got featured in Microsoft security researcher Hall of fame. If you can't find me here because this page updates after every one month. Take a look at this archive Hall of Fame page of Microsoft. They also send me MSRC Swag.
I express gratitude toward the Microsoft security team and I might likewise want to thank you for your valuable time. If you have any questions or suggestions then please use the comment form below and let me know. I always appreciate your recommendations and suggestions.








Top comments (0)