🛑 Myth: "Every pod in Kubernetes must need a service account to function."
✅ Reality: A service account is only needed when a pod needs to communicate with the Kubernetes API server or requires an identity for authentication.
But, Kubernetes assigns one to every pod by default.
🔍 Why does Kubernetes do this?
Some workloads need to interact with the API server (e.g., retrieving secrets, managing resources, scaling applications).
Kubernetes enforces a secure-by-default approach, ensuring every pod has an identity—even if it never uses it.
It follows RBAC (Role-Based Access Control) best practices, restricting what workloads can do in the cluster.
⚠️ But what if my pod doesn’t need API access?
Even if your pod doesn’t interact with the Kubernetes API, it still gets a default service account. You can’t remove it, but you can strip its power to improve security.
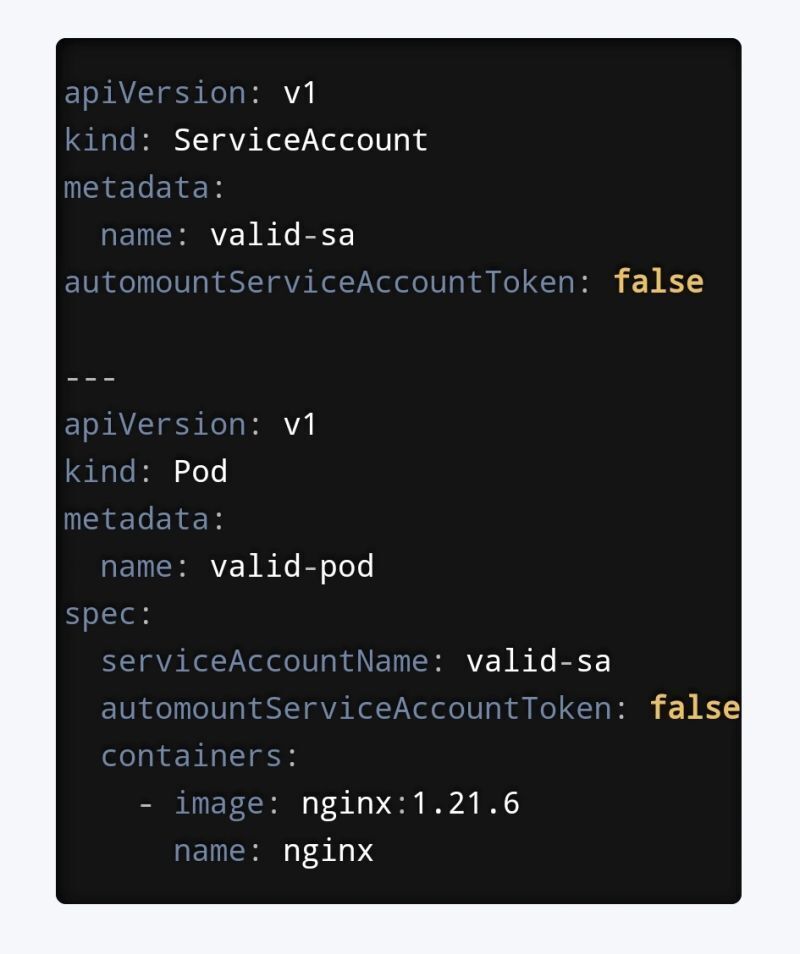
You can disable token mount at two levels, Pod level and SA level.
🔍Which One to Use?
Use pod-level: When you only want to restrict specific pods.
Use SA-level: When you want to enforce the restriction namespace-wide for all pods using that SA.
Tip: If both are set, the pod-level setting takes precedence.
💡 Bottom Line: You can’t remove the service account itself, but you can make it powerless by removing its token.
This is a simple yet effective way to reduce unnecessary attack surfaces in your cluster.






Top comments (0)