1. Hash Values (Trivial)
Popular hash algorithms include:
- MD5: widely used with a 128-bit hash value, and not considered cryptographically secure.
- SHA-1: produces a 160-bit hash string as a 40 digit hexadecimal number, banned for digital signatures since 2013 as it is prone to bruteforce attacks
- SHA-2: designed to replace SHA-1, produces a 256-bit hash string as a 64 bit hexadecimal number
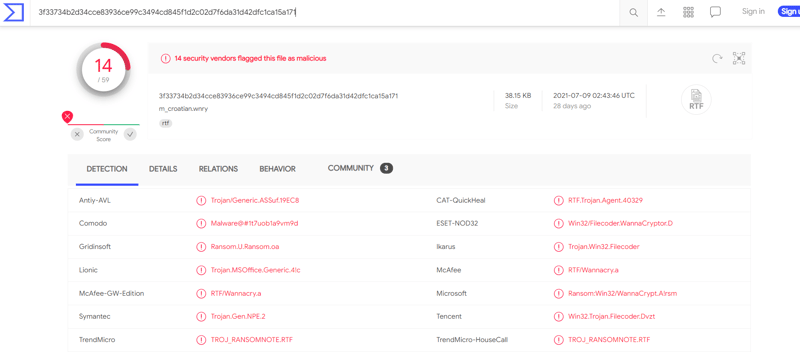
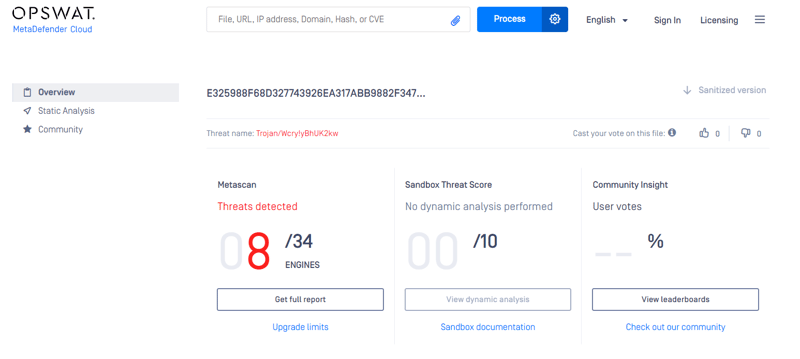
We can do hash lookups using VirusTotal and Metadefender Cloud - OPSWAT.
VirusTotal:
MetaDefender Cloud - OPSWAT:
The thing about hashes are that their values change dramatically upon modifying its original data, making many variations of the same malware that exhibits similar behavior.
2. IP Addresses (Easy)
According to Akamai, Fast Flux is a DNS technique employed by botnets to obscure activities such as phishing, web proxying, malware distribution, and malware communication. It operates by using compromised hosts as proxies, making it difficult for security professionals to detect communication between malware and its command and control (C&C) server.
The core idea behind a Fast Flux network is the continuous rotation of multiple IP addresses linked to a single domain name.
Note: AnyRun reports have IP addresses and Domain Names towards the end of the reports, so we can look into the IP reputation that way.
3. Domain Names (Simple)
Think of domain names as a name tag for an IP address.
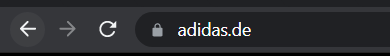
Below shows example DNS of adidas.de
Can you spot anything malicious in the above screenshot? Now, compare it to the legitimate website view below:
This is known as Punycode. What you saw in the URL above is adıdas.de which has the Punycode of http://xn--addas-o4a.de/.
To detect malicious domains, proxy logs or web server logs can be used.
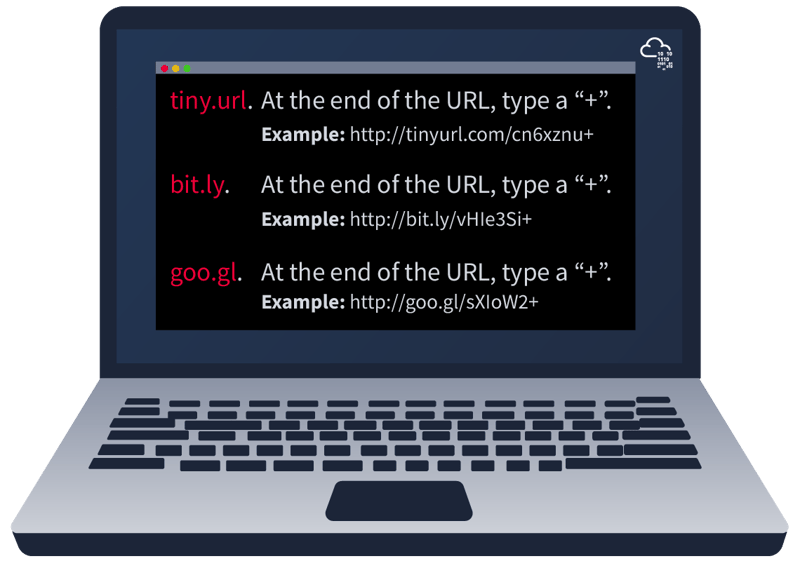
Attackers can also use online URL shortener services to generate malicious links, such as:
- bit.ly
- goo.gl
- ow.ly
You can see the actual website the shortened link is redirecting you to by appending "+" to it.
We can use Any.run to review any connections such as HTTP requests, DNS requests or processes communicating with an IP address. (sandboxing service)
4. Host Artifacts (Annoying)
Host artifacts are the traces or observables that attackers leave on the system, such as registry values, suspicious process execution, attack patterns or IOCs (Indicators of Compromise), files dropped by malicious applications, or anything exclusive to the current threat.
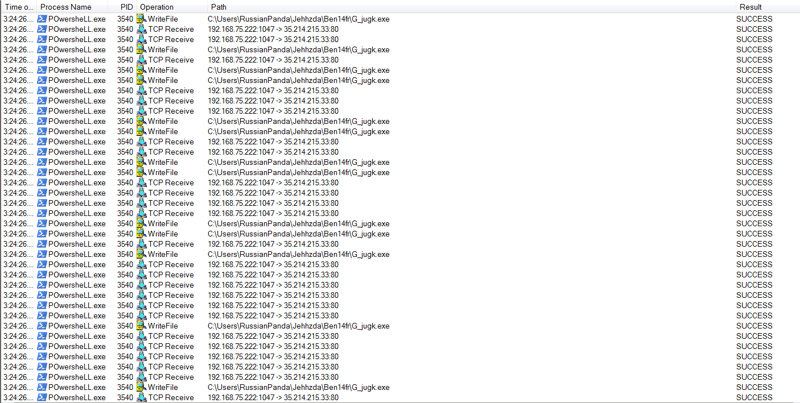
Suspicious process execution from Word:
Suspicious events followed by opening a malicious application:
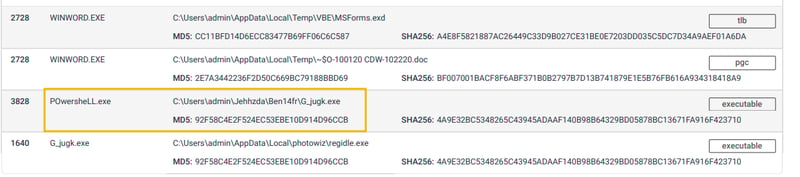
The files modified/dropped by the malicious actor:
5. Network Artifacts (Annoying)
A network artifact can be a user-agent string, C2 information, or URI patterns followed by the HTTP POST requests. An attacker might use a User-Agent string that hasn't been observed in your environment before or seems out of the ordinary. The User-Agent is defined by RFC2616 as the request-header field that contains the information about the user agent originating the request.
Network artifacts can be detected in Wireshark PCAPs (file that contains the packet data of a network) by using a network protocol analyzer such as TShark or exploring IDS (Intrusion Detection System) logging from a source such as Snort.
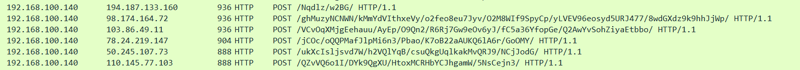
HTTP POST requests containing suspicious strings:
Let's use TShark to filter out the User-Agent strings by using the following command: tshark --Y http.request -T fields -e http.host -e http.user_agent -r analysis_file.pcap
• tshark: The command-line network protocol analyzer (part of Wireshark).
• --Y http.request: This applies a display filter to only show packets that are HTTP requests.
• -T fields: Specifies that only selected fields should be displayed, rather than the default packet summary.
• -e http.host: Extracts the Host header from HTTP requests (the website or server being accessed).
• -e http.user_agent: Extracts the User-Agent header (information about the client’s browser, OS, etc.).
• -r analysis_file.pcap: Reads packets from the given PCAP file (analysis_file.pcap).
Use Case:
This command is useful for analyzing web traffic in a PCAP file, specifically:
1. Identifying which hosts (websites) were accessed.
2. Determining the User-Agent (browser and OS) used in the requests.
These are the most common User-Agent strings found for the Emotet Downloader Trojan
If you can detect the custom User-Agent strings that the attacker is using, you might be able to block them, creating more obstacles and making their attempt to compromise the network more annoying.
6. Tools (Challenging)
Attackers would use the utilities to create malicious macro documents (maldocs) for spearphishing attempts, a backdoor that can be used to establish C2(Command and Control Infrastructure), any custom .EXE, and .DLL files, payloads, or password crackers.
For detection rules, SOC Prime Threat Detection Marketplace is a great platform, where security professionals share their detection rules for different kinds of threats including the latest CVE's that are being exploited in the wild by adversaries.
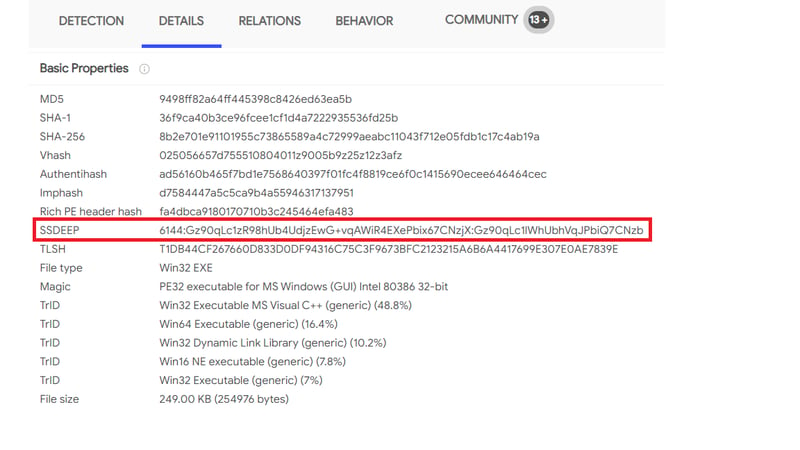
Fuzzy hashing is also a strong weapon against the attacker's tools. Fuzzy hashing helps you to perform similarity analysis - match two files with minor differences based on the fuzzy hash values. One of the examples of fuzzy hashing is the usage of SSDeep; on the SSDeep official website, you can also find the complete explanation for fuzzy hashing.
Example of SSDeep from VirusTotal:
7. TTPs (Tough)
TTPs stands for Tactics, Techniques & Procedures. This includes the whole MITRE ATT&CK Matrix, which means all the steps taken by an adversary to achieve his goal, starting from phishing attempts to persistence and data exfiltration.
If you can detect and respond to the TTPs quickly, you leave the adversaries almost no chance to fight back. For, example if you could detect a Pass-the-Hashattack using Windows Event Log Monitoring and remediate it, you would be able to find the compromised host very quickly and stop the lateral movement inside your network.







Top comments (0)